linux:ipsec:example:ss1:nftables_ruleset
Nftables ruleset of Example Site-to-site VPN topology
Address-based VPN traffic distinction
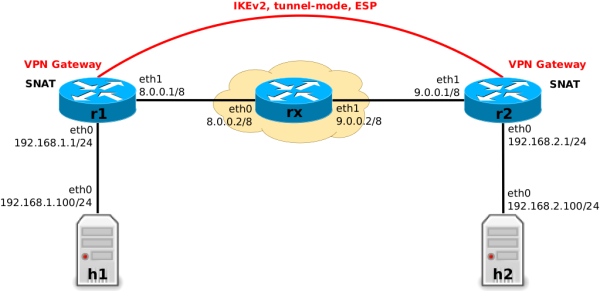
The following are the complete Nftables rulesets for both VPN gateways r1 and r2 in the example setup described in article Nftables - Netfilter and VPN/IPsec packet flow. The distinction between VPN and non-VPN traffic is done based on the peer subnet addresses.
r1
root@r1:~# nft list ruleset table ip nat { chain postrouting { type nat hook postrouting priority srcnat; policy accept; oif eth1 ip daddr 192.168.2.0/24 accept oif eth1 masquerade } } table ip filter { chain forward { type filter hook forward priority filter; policy drop; iif eth0 oif eth1 accept iif eth1 oif eth0 ct state established,related accept iif eth1 oif eth0 ip saddr 192.168.2.0/24 ct state new accept } }
r2
root@r2:~# nft list ruleset table ip nat { chain postrouting { type nat hook postrouting priority srcnat; policy accept; oif eth1 ip daddr 192.168.1.0/24 accept oif eth1 masquerade } } table ip filter { chain forward { type filter hook forward priority filter; policy drop; iif eth0 oif r2 accept iif eth1 oif r2 ct state established,related accept iif eth1 oif r2 ip saddr 192.168.1.0/24 ct state new accept } }
linux/ipsec/example/ss1/nftables_ruleset.txt · Last modified: 2022-01-30 by Andrej Stender